Transforming War with Meshed Civil-Military Sensor Networks (I)
Ukraine and Intensified Multi Domain Operations
The war in Ukraine is an aggregation of many old ideas about war. Ground combat, the use of armoured vehicles, artillery, electronic warfare and the importance of tactical logistics are old themes in war. So too are the more human elements – the importance of individual and collective training, good doctrine and tactics and the centrality of excellent leadership.
But all wars also add a few new technologies and ideas to these many old – or even ancient elements. In the Second World War, we witnessed the birth of global, total war, the exploitation of electronic warfare, and the destruction of cities by firebombing and nuclear weapons. In the first Gulf War, the introduction of immature computerised command and control as well as stealth aircraft was new.
During the war in Ukraine, there have been at least three important developments that will transform the character of war. These are:
The widescale integration of autonomous systems into tactical and strategic operations.
The widespread adoption of digitised command and control systems that connect fires, recon, logistics and other battlefield functions.
A new era meshed network of civilian and military sensors, analytical capabilities and dissemination systems.
Each of the three is a combination of new technologies, some older mechanisms as well as new and evolved concepts and organisational approaches that apply and exploit technologies in innovative ways.
This article, and the one that follows, explores this new era meshed civil-military network of sensors, analysis and distribution in Ukraine, and their wider impact on military affairs. This developing system portends massive changes in how military institutions prepare for war, how they organise, how they train and educate their people, and how they execute military operations and campaigns. This is because such a system offers an order of magnitude reduction in the time between detection and destruction of many battlefield targets.
But at the same time, the highly integrated capacity of the almost pervasive civil and military sensors that exists on the ground, in the air and in space represents a vulnerability in military systems which must be protected.
What is the Meshed Sensor Network?
Military organisations have always relied on communications, and networks, to inform themselves about the strength and locations of their adversaries, supply locations, routes, and information about themselves. Whether it was Alexander’s campaign through central Asia or Ukraine’s ongoing campaigns, the collection, assessment and flow of information is the lifeblood of military organisations.
The development of the internet and satellite communications has enabled the construction of dense networks that permit humans, and military institutions, to communicate instantly, maintain awareness of the world around them, and to access a quantity and quality of information that is unprecedented in human history.
Military and civil communication networks play an important function in military operations. Networks carry and fuse sensor data used by analysts and commanders. Networks also provide the entry point for those who might wish to interfere with the perceptions of military staff and commanders by inserting false data or cutting off that data altogether as part of a deception plan.
The concept of network centric warfare (or NCW), originated in the system of systems work of Admiral Owens in the 1990s. The concept of NCW, and the associated idea of ‘information superiority, quickly caught on. It thereafter resulted in significant academic, doctrinal and equipment procurement in the United States and beyond to create information age ideas about connecting, fighting and organising military institutions. As Dave Alberts wrote in Network Centric Warfare: Developing and Leveraging Information Superiority:
War is a product of its age…warfare in the information age will inevitably embody the characteristics that distinguish this age from the previous ones.
Technology since the original work on NCW has developed at a rapid pace. The military and other networks of the third decade of the 21st century are more capable, and generate much more data, than even the visionaries of NCW imagined. Radios, computer networks, satellite constellations and ground stations, encryption technologies, data management, artificial intelligence, and high-performance computing are among some of the technologies that are now integrated into sensor and communications networks.
But it is the interaction of military forces where interesting signature detection using civilian assets has come to the fore. For example, many commentators and analysts now use the US National Aeronautics and Space Administration (NASA) Fire Information and Resource Management System, available online, to assess the level of artillery fire missions in Ukraine. And because Russians have often resorted to insecure communications during their invasion, amplified by a Russian milblogger community, civilian operators as well as military intelligence agencies have been able to intercept, analyse and share sensitive military discussions.
Open-source satellite data is also playing a role in not just Ukraine operations, but also in measuring more strategic activities. Over the past 18 months, civilian analysts have used satellite imagery to chart the progress of Russian and Ukrainian military forces. There has been a massive expansion in open source battle tracking since February 2022.
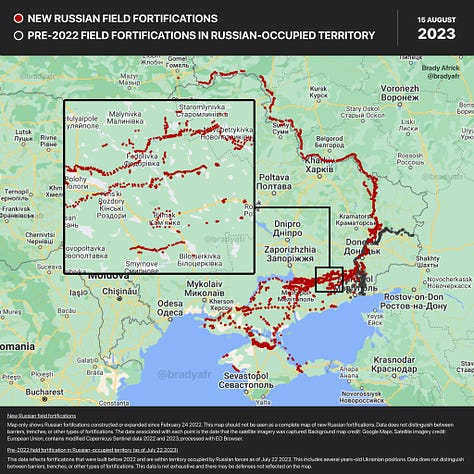
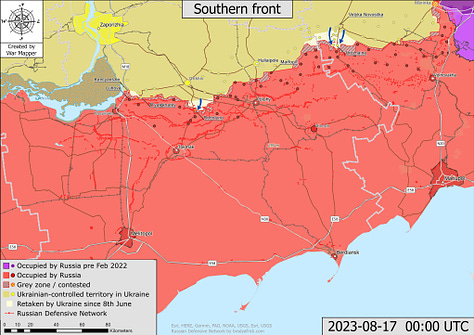
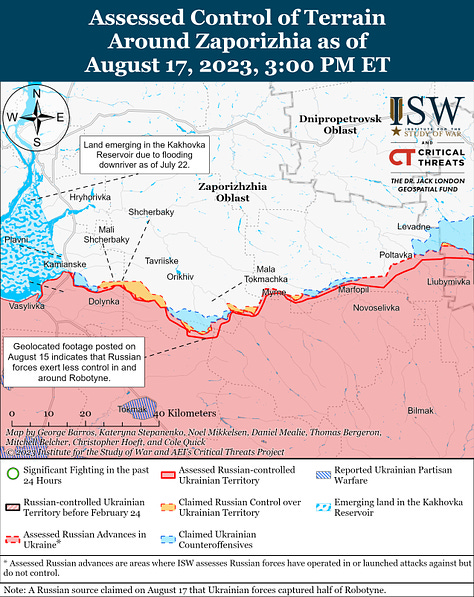
Beyond the war in Ukraine, open-source satellite imagery has also been used to detect and monitor Chinese construction of islands and bases in the south China Sea - a signature difficult to hide - and monitor the construction or maintenance of ships for the PLA Navy and the Russian Navy. They might also be used to monitor training activities (to assess readiness and leadership capabilities) as well as equipment status and posture prior to deployments.
Finally, data from civilian technologies can provide a signature that might be exploited by unfriendly actors. The Strava information leak, which has led to the mapping of several US facilities overseas, is just one example of consumer device signatures having an impact on military activities – and the ability of military forces to minimise their signatures. Another example of this trend has been the huge number of civilian drones used by both sides having an impact on military operations, although they also bring with them vulnerabilities such as the level of security between drone and operator, and hardening against electronic warfare.
Open-source sensors often utilise older versions of contemporary military technology. And as the NASA FIRMS demonstrates, these provide only rough approximations of events that might be related to military activity. But intelligence activities – and busting through deception measures – is about assembling multiple layers of information to build a complete picture or hypothesis of what those layers mean. The ability of open-source sensors, often used by civilian intelligence agencies such as Bellingcat, to detect military activity means that military institutions must be even more careful and cleverer with their signatures in the 21st century.
But it is not just the sensors in this mesh that are of interest. Over the last decade, there has been growth in the civil intelligence analysis that uses the data collected by these networks. Military intelligence has long focussed on a cycle that includes collection, analysis and dissemination of useable information. Now, multiple civilian intelligence agencies operate in parallel – and sometimes in partnership – with military and other government intelligence agencies. Examples of these organisations include Belligcat, Dataminr, and the Institute for the Study of War. These institutions are supplemented by a myriad of individuals that also undertake analysis of the Ukraine war and distribute their products online.
The products of the meshed civil-military intelligence analysis are used by military and other national security organisations. One example is the daily assessments produced by the Washington DC-based Institute for the Study of War (ISW). High quality daily reports and mapping products are produced by ISW and distributed on the internet and through social media. These products are used by Government agencies to supplement more classified sources. They have been used in Congressional testimony in the US. Additionally, these assessments are widely used by combat units in Ukraine to supplement intelligence from official sources which is either slower in dissemination, or of lower quality.
Meshed sensor networks have six elements, each of which is increasingly underpinned by artificial intelligence support:
The sensor elements that collect data on what is happening.
A communications element that transmits information between systems and operators.
A security element that ensures that data, as well as the links that connect sensors and analysts, are secure from spoofing, data corruption or data theft.
A processing element/s, which aggregates and analyses data from many sources to inform decision making.
A decision element, currently human, where information is turned into action.
An effects component, where information and decisions are turned into kinetic and non-kinetic effects on the battlefield or in other strategic endeavours.
One of the key impacts of this has been a closer integration of different domains in joint operations, better coalition connectivity, and a better synthesis of military and non-military activities in a multi-domain, whole of nation construct.
The Meshed Network Intensifies Multi-Domain Operations
Over the past century, the domains in which humans compete and fight have broadened from the age-old ground, information and maritime environments.
The introduction of aircraft at the beginning of the 20th century was just the beginning of this expansion of warfighting domains. These fighting are now complemented by space, air and cyberspace. This concept of deepening integration with one of the seven key trends in military affairs that I explored in detail in my 2022 book, War Transformed.
And while more joint operations have been a key theme across the past century, more integrated thinking at higher levels has also been crucial to generating effective military institutions as well as successful national warfighting efforts.
After the First World War, the concept and practice of strategy broadened from a military endeavour to one that was a national undertaking. This included industry and other elements of national power. Since the end of WW2, there has been a continuing shift to a more unified approach in military operations through the development of joint concepts and institutions.
There have been various drivers for this shift towards a more integrated approach for military and national security affairs. These include military necessity (particularly for smaller military institutions such as Australia or the UK) and political imperatives (such as the 1986 Goldwater Nicholls Act) that fundamentally redeveloped the structure and operating of the US Department of Defense.
Further impetus was provided by the very successful US military and its coalition partners in the 1991 operations against Iraq. This first Gulf War, and the rapid coalition victory over the Iraqi military, was testament to the benefits of a more joint, integrated approach to military operations.
Despite this, in the past two decades, military institutions undertaking counter insurgency and national building operations have rarely had to operate in more than two or three domains concurrently. The war in Ukraine, and strategic competition with China, has shown that contemporary military organisations must operate in all five domains concurrently.
In Creating Military Power, Risa Brooks and Elizabeth Stanley reinforce this point, describing ‘integration’ one of their core elements of military effectiveness. In contemporary operations, and in likely future contingency, military forces are more likely to have to fight in all domains concurrently.
Consequently, ideas like joint operations, the British 2020 Integrated Operating Concept 2025 or even the concept of Mosaic Warfare explored by the U.S. Defence Advanced Research Projects Agency (DARPA).



Importantly, our potential adversaries have recognised this integration trend. As two Chinese Colonels, Qiao Liang and Wang Xiangsui, explored in Unrestricted Warfare in 1999, the authors define the future battlefield as “everywhere”:
Technology is again running ahead of the military thinking. While no military thinker has yet put forth an extremely wide-ranging concept of the battlefield, technology is doing its utmost to extend the contemporary battlefield to a degree that is virtually infinite: there are satellites in space, there are submarines under the water, there are ballistic missiles that can reach anyplace on the globe, and electronic countermeasures are even now being carried out in the invisible electromagnetic spectrum space. Even the last refuge of the human race--the inner world of the heart--cannot avoid the attacks of psychological warfare. All the prevailing concepts about the breadth, depth and height of the operational space already appear to be old-fashioned and obsolete. In the wake of the expansion of mankind's imaginative powers and his ability to master technology, the battlespace is being stretched to its limits.
The environment that is described here is now being witnessed in Ukraine, where both Ukrainian and Russian operations feature a significant degree of integration across the physical and non-physical domains. It is also a key feature of contemporary Chinese military development of warfighting concepts. Their recent development of Systems Destruction Warfare is a recognition of the power of integrated warfare, and the centrality of denying this capability to their adversaries.
For Western military institutions, a key outcome of this more integrated approach, at the tactical and operational levels, is to resist and overcome Chinese and Russian advantages in precision, long range attack systems (including kinetic, cyber and influence activities). At the strategic and political levels, it should provide for more coherent policy making, allocation of resources and alignment of military and other national security activities with desired national objectives.
Clausewitz wrote in On War that “war is never an isolated act”. The closer integration of military, other government organisations and defence industry to achieve national outcomes is a contemporary imperative. And while there is a national security imperative for this, this closer integration also demands high levels of trust and very skilled collaborative planning.
Transforming War
The ongoing development of more integrated methods of strategy development and execution is given additional impetus by the strong possibility of authoritarian states seeking to gain strategic advantage in non-military areas of power.
Western military institutions, in partnership with other arms of government and international partners, must build and protect friendly systems while breaking down enemy systems. One of the key foundations for this systems approach to war is high quality, assured situational awareness. Fighting for, and with, information has always been a priority for military commanders and institutions. The availability of different sensors and analytical tools to civilian organisations of a kind only previously available in small niches of military institutions, portends a transformation in the character of warfare.
This will have an array of impacts, including in individual training and education, the organization of single-domain and joint institutions, collective training, warfighting and combat support concepts, and strategy.
But before exploring these impacts in more detail, there is another aspect of this new-era meshed sensor, analysis and distribution system that needs to be explored in the second part of this article.
This is the 21st century signature battle.
(Part II of this article will be published over the weekend of 19-20 August 2023)





I am a former US Army 98G (now 35P) and SIGINT/EW history is one of my subject areas as a mlitary historian. Radio communications, "hybrid war," artillery, and the struggle to restore movement are indeed the definitive modern military revolution. I've written seminar papers about examples from 1914 to the present. I appreciate that you appreciate the vital importance of the 4th dimension to the modern battlefield.
All of which is to say that taking a single-channel radio into combat is like taking your musket in the 21st century. Looks nice, just using it will probably get you killed.
Thank you for this, sir. Took a lot of books from this - excited for the follow up, and analysis of impacts.