Transforming Warfare with Meshed Civil-Military Sensor Nets (II)
Ukraine and a New-Era Signature Battle
In first part of this article, I explored the development of a new era meshed sensor system, which has seen its development accelerated by the war in Ukraine. The previous article defined what this new meshed sensor system is, and how it was having an impact on the increasing integration of military activity and multi domain operations.
This meshed sensor system has six components:
The sensor element that collects data on what is happening.
A communications element that transmits information between systems and operators.
A security element that ensures that data, as well as the links that connect sensors and analysts, are secure from spoofing, data corruption or data theft.
A processing element/s, which aggregates and analyses data from many sources to inform decision making.
A decision element, currently human, where information is turned into action.
An effects component, where information and decisions are turned into kinetic and non-kinetic effects on the battlefield or in other strategic endeavours.
This article explores the intensified signature battle, and the impact of the new meshed sensor system on how nations prepare for, deter and fight wars.
The Meshed Sensor Network Intensifies the Signature Battle
This development and accelerated deployment of an expanded meshing of civilian and military sensor networks will perhaps have the greatest impact on what I describe in War Transformed as the Battle of Signatures.
Every piece of military hardware possesses a signature. This might be visual, aural or in the electromagnetic spectrum. It might be all of these as well as possess signatures such as vehicle or aircraft exhaust.
Military units, at different scales, also have signatures. These include patterns of operations and exercise schedules as well as the indicators for impending military activity. The core idea for future military organisations is to minimise their tactical to strategic signatures, use recorded signatures to deceive, and be able to detect and exploit adversary signatures – across all the domains in which humans compete and fight.
This has resulted in an ongoing signature battle, which has intensified and accelerated with the development of meshed military-civilian sensor systems. The technological sophistication of potential adversaries, their mass, and their presence in every domain of war mean that the battle of military signatures will be one of the defining aspects of deterring and conducting war in the twenty-first century.
As I noted in my explorations of this trend, those institutions that can used meshed sensor networks to collect information on the signatures of military organizations and turn this information into timely, actionable products will possess a decisive advantage. This advantage will accrue on the battlefield, the conduct of campaigns and in strategic planning.
In Ukraine, the signature battle (which incorporates meshed sensors, digitised command and control and pervasive autonomous systems) has manifested as a closing of the detection to destruction time to periods that can approach one minute. This is unprecedented in warfare. At the same time, this signature battle has enabled the detection of tactical and operational high value targets that is used to prioritise the use of scarce precision munitions.
There are many lessons to be drawn from how Ukraine and Russia are able to mesh their sensor networks to detect a variety of different signatures and turn this into actionable intelligence. These lessons are likely to have a significant impact on force structure, mobility and survivability of future military organisations in the field and at home locations. Just a few examples of the impacts on force design include mobility of high value targets, emissions standards for communications and more distributed operations and support concepts.
But that is for the future. Right now, there is an important case study in the use of meshed sensors and the signature battle from southern Ukraine: the Ukrainian advance through the Surovikin Line.
Case Study: Breaching the Surovikin Line
This meshed sensor system has had a significant impact on the Ukrainian 2023 offensives.
The scale and number of mines and obstacles in southern Ukraine, and increasingly in the east as well, is very daunting. One can look at a satellite map or overlay to gain some appreciation of the challenge, but it is another thing entirely to plan and execute operations to physically have to penetrate it. The Russian obstacle design is more complex, and deadly, than anything experienced by any military since World War Two. It is tens of kilometres deep, which will break up or slow down even the most competent combined arms teams and separate them from their logistic support.
In a previous article, I covered this Russian doctrine for the defence in some detail, including the doctrinal templates that lay down the development of obstacle belts and deployment of defending forces. You can read that article from 23 June (The State of the Ukrainian Campaign) here.
That said, the construction of the Surovikin Line has been observed by military and civilian sensors, including aerial and space-based assets, since the end of 2022. The scale of the challenge has evident as it has been measured continuously as the different defensive lines were built over the past eight months. Brady Africk is just one of the many talented analysts who have followed this closely and his posts from December 2022 and August 2023 are shown below.
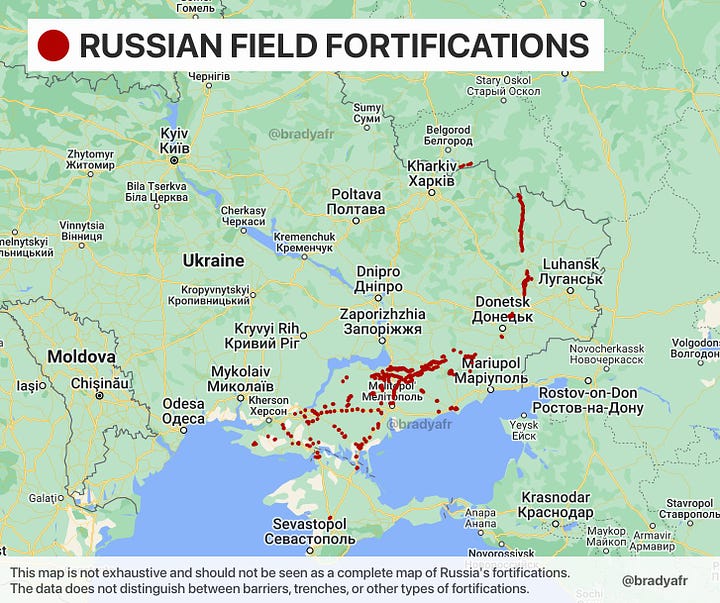
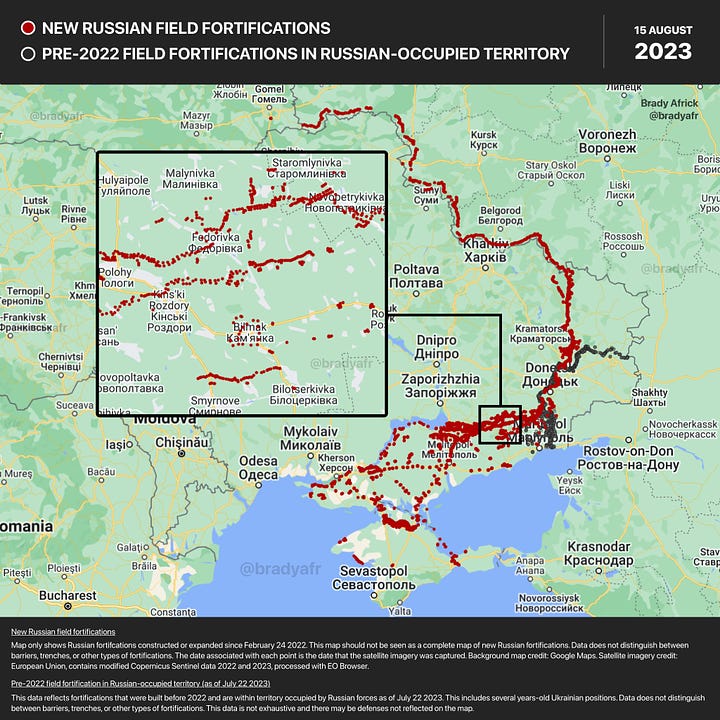
In previous wars, this might have been possible for military institutions, but not for civil institutions. Additionally, the level of detail now available through open-source satellite imagery, supplemented with open-source reporting on Russian units, social media images and chatter on Russian telegram channels, has provided non-military analysts and citizens with an unprecedented picture of the Surovikin Line.
There is little doubt that many open sources of information were used in the planning of the Ukrainian 2023 offensive. The profusion of freely available sources about the Russian defensive lines, unit status and dispositions, and other subjects from Russian milbloggers will have been a treasure trove for Ukrainian (and Western) intelligence analysts. This is probably the reason why there has been a recent crackdown on these milbloggers, as well as on Russian citizens more generally who might share images of Ukrainian attacks on social media. As a 16 August 2023 ISW report notes:
Russian Federation Council Committee on Constitutional Legislation and State Construction Head Senator Andrey Klishas stated on August 16 that a group of Russian senators has proposed an amendment to the laws “On Mass Media” and “On Information, Information Technology and Information Protection” prohibiting the distribution of photos or videos of Russian troop deployments and redeployments, military infrastructure, the location of critical facilities, and videos or photos that could be used to confirm the defeat of an element of the Russian military.
Unfortunately, this meshing of sensors for the signature battle works for both sides.
Despite the very good operational security shown by the Ukrainian Armed Forces in the lead up to the offensives, Russian intelligence agencies would also have used many open sources to ascertain the most likely Ukrainian tactical and operational objectives. They would probably have used open sources to track the formation of new brigades, the provision of western equipment and where training was being conducted so training bases in Ukraine could be attacked.
The Russians have also leveraged this new era sensor network to ensure that observation of their obstacles is pervasive. In a recent article I called Breach and Breakthrough, I explored how obstacles must be covered by ‘observation and fires’. Throughout the war there has been a steady intensification of sensors, analysis and dissemination of intelligence through this new-era meshed civil-military framework.
Compounding this challenge, this meshed sensor framework is linked to artillery, longer range rockets, attack rotary and fixed wing aircraft, loitering munitions, scatterable mines and electronic warfare. It makes detection and targeting a very short loop for the Russian defenders and was a factor that was not present when modern obstacle breaching doctrine was developed several decades ago.
So, as good as we might become at the meshing of civilian and military sensors and analysis, this is also an approach that can and will be used by the enemy. And unfortunately, in southern Ukraine, the Russians have used it to good effect to delay Ukrainian advances on their two key axes of advance.
What is to be done?
Human Solutions to the Challenges of Meshed Networks: The Battlefield and Beyond
The Battlefield. One approach that addresses the increased lethality resulting from the battle of signatures is distributed operations. Distributed operations deceive an enemy about capacity to concentrate and force structure because distributed elements can be grouped, disaggregated and then regrouped according to mission and threat profile of the enemy. This is useful in operational and tactical activities is because it supports enhanced force preservation and survivability against technologies that have increased the lethality of the contemporary battlefield.
The United States Marine Corps has experimented extensively with the concept of Distributed Operations. Developed by the USMC Warfighting Laboratory, it is a warfighting concept that is designed to disperse a networked force across the breadth and depth of the battlespace. This dispersal lowers its overall operational signatures while enhancing its survivability and reach. This concept was incorporated in the 2017 USMC/US Navy’s concept of Littoral Operations in a Contested Environment. It was then further refined and subject to experimentation and issued as the most recent USMC Warfighting concept called Stand In Forces, in December 2021.


It is a good example of how the current trend of meshed sensors and the signature battle are influencing force design and warfighting concepts in contemporary military organisations.
However, increased lethality has been a trend for at least the last 200 years of human conflict. The dawn of the First Industrial Revolution at the end of the 1700s saw a significant change in historical patterns of battlefield lethality. Starting in the 1800s, the trend in lethality commenced a sharp upward curve.
This increaed lethality was countered through increasing the dispersion of individuals and military units within a cohesive force. This lowered average daily casualty rates in war and enhanced the survivability of important capabilities such as headquarters and logistics nodes. This trend of increasing lethality and then increased dispersion is explored by Trevor Dupuy in his book The Evolution of Weapons and Warfare (1984).
In short, technological progress in finding and killing an adversary over the past two centuries has been offset by an intellectual response.
In addition to decreasing the potential lethality of enemy operations, dispersion of forces through distributed operations allows for more opportunities to deceive an adversary. This is because a more dispersed force provides fewer insights into friendly main and supporting efforts due to a lack of concentrated forces. Distributed operations also distribute logistics and fire support assets, again deny an enemy detailed insights into main efforts, and deceiving them about friendly intentions for a longer period than might otherwise be the case with more traditional operational approaches.
As well as considering distributed operations, military operations must prioritize the projection of false signatures (digitally as well as with dummy equipment) to overwhelm or at least confuse adversary analysts and AI analytics about friendly locations, capabilities, and intentions.
New types of adaptive camouflage, vehicle shaping, cyber warfare, and interference will need to be developed to counter the new sensor technologies. This must be accompanied by a reinvigorated capacity by Western military and political leaders to deceive adversaries actively and consistently.
More broadly, operations should target all six elements of an adversary sensor network described earlier, although priority must be afforded to degrading the performance of the sensor, analytical and decision-maker elements. These are likely to provide the best operational return for investment in time, focus and deployed capabilities.
Despite the advances of this meshed network, there is unlikely to ever being an ‘unblinking eye’ on all human activities and intentions, the increasingly ubiquitous and pervasive nature of sensors – military and civilian – mean that the vast majority of military signatures can be detected in near real time. Tactical forces will require new masking techniques to minimize their potential of detection. There is no chance of eliminating that potential entirely given the wide-scale proliferation of sensors in civil-military mesh.
Information Warfare. The pervasiveness of social media users in nearly every environment in which humans will fight (except possibly space, and even that could change) means military commanders and planners must incorporate the threats and opportunities of social media into the planning processes. Assumptions must be made in formal planning and decision making about the level of visibility that social media might provide over military operations, and the levels of deception that might be required to prevent or minimise it.
The application of deep fakes by potential adversaries could impact on the credibility of national leaders, and their communication with their citizens, in situations of competition and conflict. The use of advanced AI to create these will necessitate counter-deep fake technologies in military and other national security institutions to ensure that flooding the internet with deep fakes doesn’t impact on the ‘cut through’ of actual national strategic messaging, and subsequently dissuade populations from supporting national competition or war efforts.
Command, Leadership and Personnel Development in a Meshed Environment
The meshed civil-military system will have an influence on command and control of military institutions and forces. There must be a high level of advocacy, and emphasis on, understanding the opportunities of this approach by senior military leaders. At the same time, the development of military and other national security leaders must focus on developing those skills that minimise those leaders ‘deceiving themselves’ through bias, lack of input and other cognitive issues.
At the same time, meshed operations hold the potential to challenge civil-military relations in democracies that value transparency and accountability in the many elements of government. As such, senior military leaders must have discussions with political leaders on the rationale for such approaches, and to ascertain the legal and ethical limitations that might be placed on the conduct of meshing civil and military sensors and analytical capabilities. For example, one question that might be addressed is whether a civilian that uses an smart device app to report an enemy drone is a combatant or not. There are many similar issues to explore.
Finally, military and other national security leaders will need to be educated and trained in the various aspects of signature management, measurement and projection as a part of military strategy as well as meshed operations. This must include educating and training personnel to not assume that this meshed sensor network will provide total transparency of the battlespace, or certainty about future activities by an adversary. These, by definition, are impossible. The will, resilience and performance of human organisations in battle are unknowable until combat is joined.
The Ongoing Transformation of Finding – or Avoiding – a More Lethal Enemy
One of the key themes of the war in Ukraine, and war more broadly, is that it is a learning and adaptation battle. In this war, as in others, both sides have learned from their own actions and those of their enemy to produce more effective solutions to finding the enemy and destroying enemy units and assets while at the same time denying their enemy the ability to do this to them. It is a constant, yet often uneven, adaptive cycle.
The meshing of sensors and an intensified signature battle are an important aspect of the war in Ukraine. The tactics, organisations, training, technologies and other elements of its development and application must be studied by Western military institutions. These observations are likely to drive a multitude of changes in military systems. The war and its lessons are certainly being studied by our potential future adversaries.
Our aim must be to stay at least one step ahead of them.





The June or July issue of the Journal of Electromagnetic Dominance had a good article on the challenges and limitations of decentralized C2. Enlarging the use of false signatures is one way to ameliorate the threat to your TOC. However, it requires an expansion of the resources (systems, people, etc) for EW deception. Which raises an important point: as much as I enjoy seeing the US Army finally restore EW capabilities to its formations, and watching the new Compass Call take wing, I worry we are not building anywhere near enough EW capability, still. I remain unsure that there will be enough "rabbits" (false stations) and associated equpment to protect the division headquarters if the balloon goes up. I worry that our forces are not red-teaming with their own sensors. I worry that EW is becoming a basic part of soldiering, such that every troop needs their own SDR (software-defined radio), but we do not teach those skils in basic training. Same with drones.